Challenges: Balancing Encryption Strength with Computational Efficiency
Encryption and cryptanalysis, deciphering encrypted data, are also at odds. Cryptoanalysis changes to stay up with cryptographers’ ever-improving methods. This cat-and-mouse game affects data security and cryptography standards.
Advances in cryptography are crucial. Digital communication security evolves with new technologies and threats. One example is cryptographic methods that can withstand quantum computers, which could completely degrade encryption standards. As blockchain technology integrates, decentralized and secure communication potential arises (Oppliger, 2021).
Cryptography trends could transform global communication. Quantum cryptography and other encryption advances are making Internet transactions safer, more private, and more dependable. Cryptography, an ancient art and science, will grow to defend our digital world as we travel this dynamic planet.
References
Alimam, H., Mazzuto, G., Ortenzi, M., Ciarapica, F. E., & Bevilacqua, M. (2023). Intelligent Retrofitting Paradigm for Conventional Machines towards the Digital Triplet Hierarchy. Sustainability, 15(2), 1441.
Bauer, C. (2021). Secret history: The story of cryptology. CRC Press.
Javadpour, A., Ja’fari, F., Taleb, T., Zhao, Y., Bin, Y., & Benzaïd, C. (2023). Encryption as a Service for IoT: Opportunities, Challenges and Solutions. IEEE Internet of Things Journal.
Kumar, N. V., Divya, A. S., Sree, B. K., & Daniel, M. P. An Investigation on” Unlocking the Potential: Advances and Challenges in Quantum Computing.
Oppliger, R. (2021). Cryptography 101: From Theory to Practice. Artech House.
SaberiKamarposhti, M., Ghorbani, A., & Yadollahi, M. (2024). A comprehensive survey on image encryption: Taxonomy, challenges, and future directions. Chaos, Solitons & Fractals, 178, 114361.
Sawyers, R. (2021). The History of American Cryptology Before World War II.
Appendix
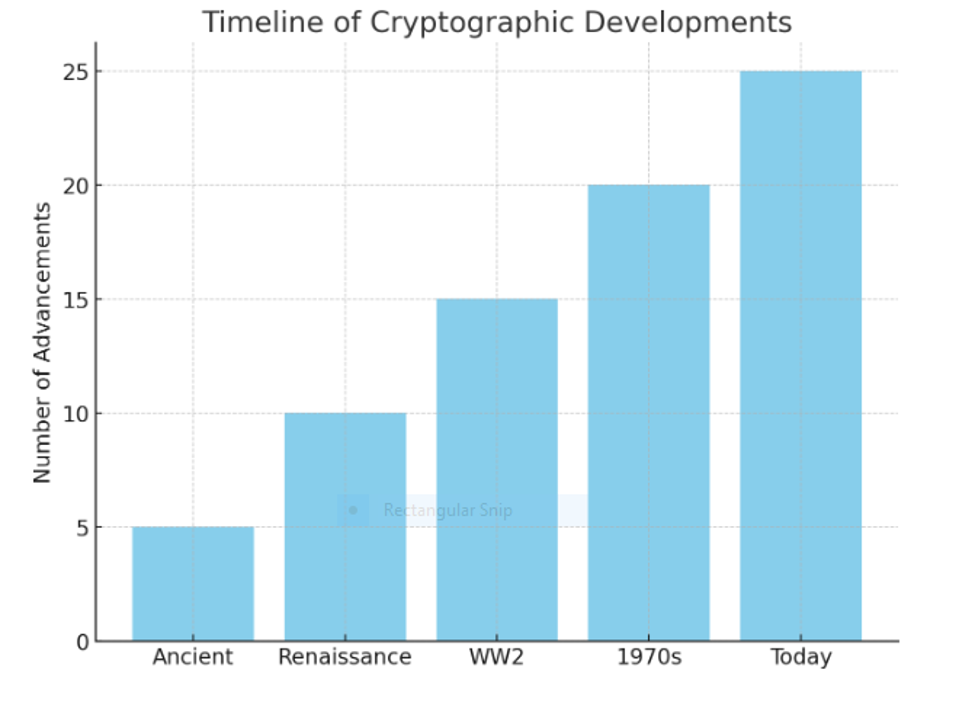
Timeline of Cryptographic Developments Bar Graph: This graph demonstrates the changing difficulty and number of cryptography advances from ancient times.
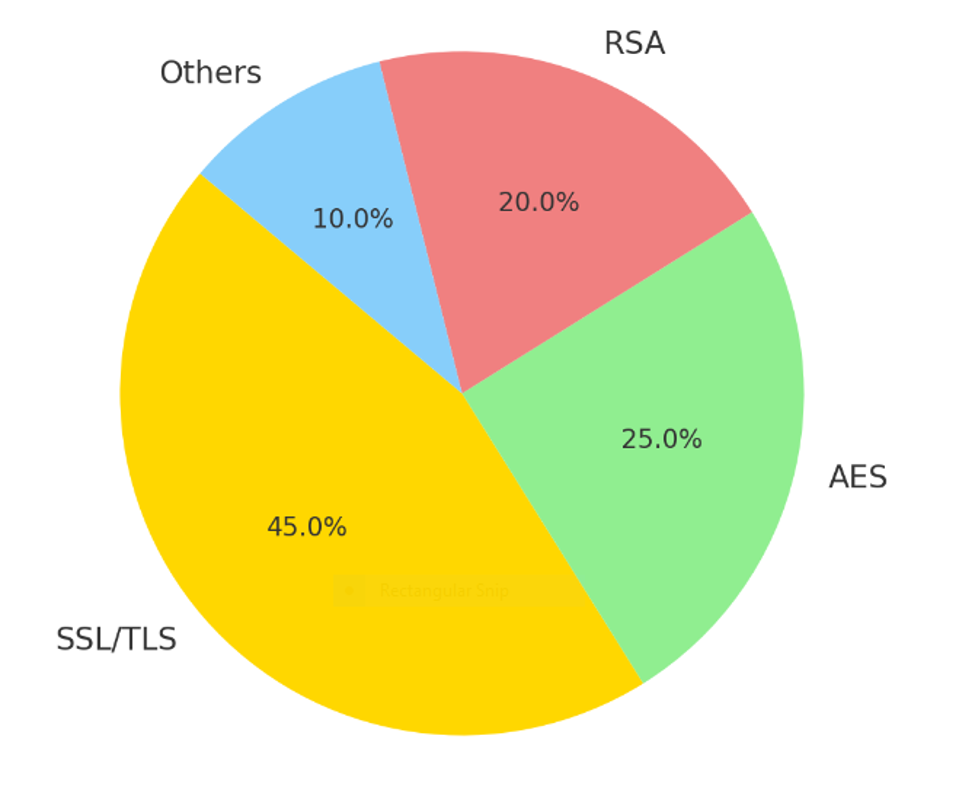
Usage of Encryption Protocols Pie Chart: SSL/TLS leads the encryption protocol list, followed by AES, RSA, and others. The many encryption technologies used to secure online communications are shown in this pie chart.
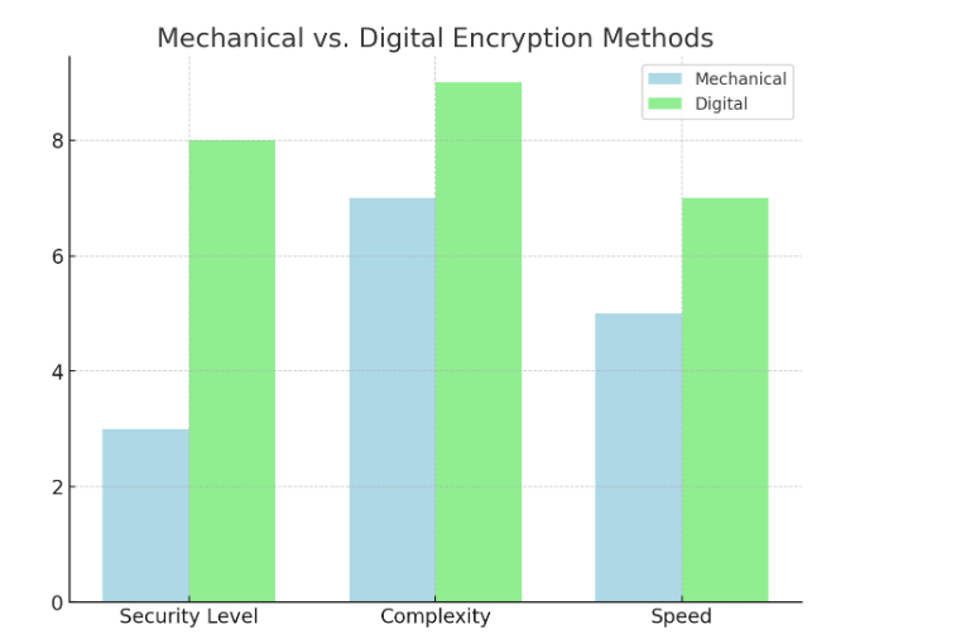
Comparison of Mechanical vs. Digital Encryption Methods Bar Graph: Digital encryption methods outperform mechanical ones in security, complexity, and speed, demonstrating encryption technology’s progress.
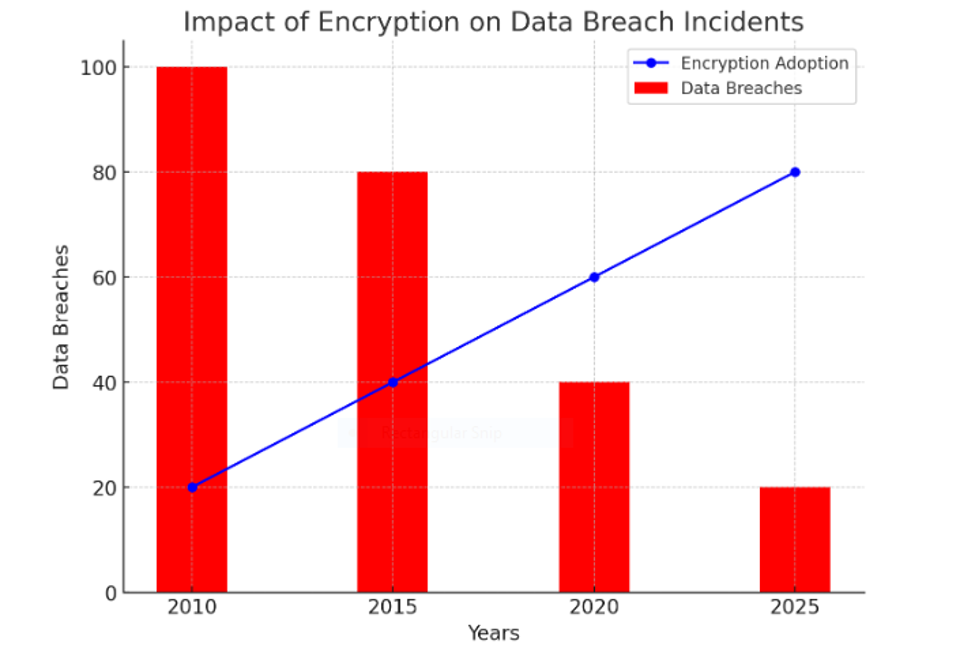
Impact of Encryption on Data Breach Incidents Bar Graph: In the graph, data breaches decrease as encryption use increases, showing a link between encryption and data security.
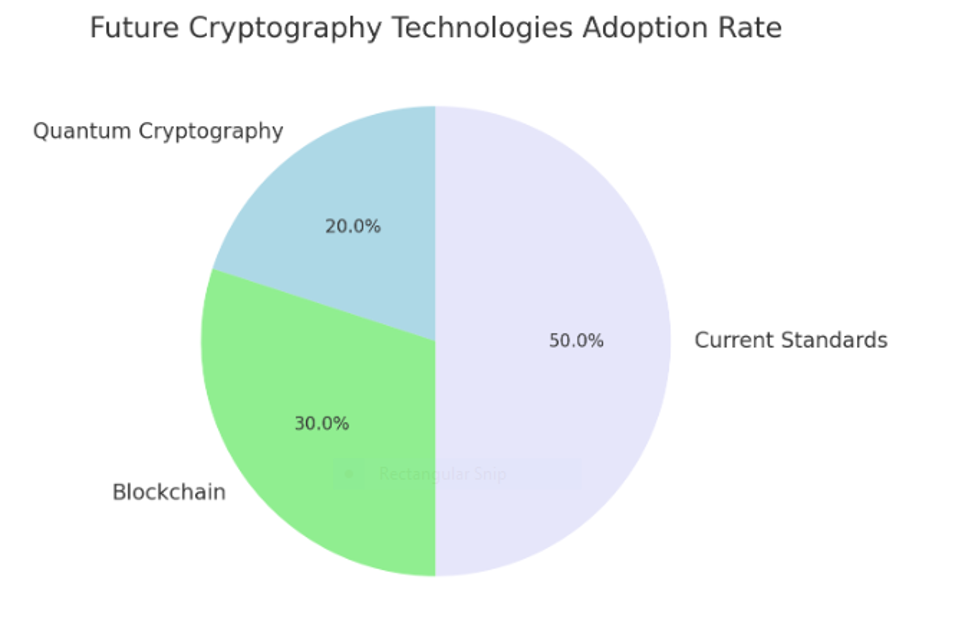
Future Cryptography Technologies Adoption Rate Pie Chart: This chart projects increasing acceptance of quantum cryptography and blockchain, along with current standards.
Don't have time to 
Use our essay writing service and save your time. We guarantee high quality, on-time delivery and 100% confidentiality. All our papers are written from scratch according to your instructions and are plagiarism free.
Cite This Work
To export a reference to this article please select a referencing style below