Create an eight (8) page Business Continuity Plan (BCP) that addresses the mission needs and systems for recovery of the whole enterprise after a cyberattack event. This BCP will be used to help the CISO identify current systems and timelines that will be used to bring systems back online and the sequence of events that occur during the deployment of the plan. Make sure that all citations are in proper APA format.
-
Business Continuity Plan – Needs and Systems for Recovery after a Cyberattack Event
Introduction
Ransomware attacks on the nation’s summit systems lead to a loss of system and data confidentiality, integrity, and availability. The Reveton ransomware denied summit attendees access to conference data, and the computer screens displayed a message indicating a system hack that outputs a message mimicking federal law enforcement authority. Notably, ransomware attacks evolve quickly, and there is no particular framework for combatting new attacks. If a system is hacked, one primarily has two options: pay the ransom or attempt system recovery by rolling back to a previous backup point. Hackers cannot be trusted to release system resources once the ransom is paid. With this in mind, the system’s protection will rely heavily on historical data copies and a wide array of protection mechanisms, as detailed below.
Identifying critical systems
Security Categorization of Summit Data and Systems
In line with the “FIPS 199: Standards for Security Categorization of Federal Information and Information Systems”, (2004), summit attendees could not access data required for the conference, and the impact can be categorized as high. Comprehensively, a “high” potential impact implies that losing availability, integrity, and confidentiality leads to catastrophic repercussions on the summit participants, organizational assets, and operations (“FIPS 199: Standards for Security Categorization of Federal Information and Information Systems Assessment”, 2004). The Reveton ransomware will probably lead to financial losses and crippled mission capability till the critical systems and services are restored.
The following process will be used to identify critical systems.
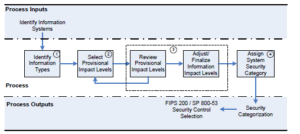
Figure 1 – Identification of critical systems.
Step 1: Identification of various information types
The incident response and recovery team will report about the summit’s mission statement and business process and note the specific types of data fed in the system, processed, stored, and output from the system. Vital activities will include identifying mission-dependent categories of data, support and management information, and other significant information categories (Stine et al., 2008). The core aspects of focus entail functions of the summit and the conference, techniques used by the nation’s summit to achieve its objectives, support functionalities needed by the summit, and information related to the management of resources.
Step 2: Determination of provisional impact levels
There are three possible categories of potential impacts: low, moderate, and high, associated with the system and its information confidentiality, integrity, and availability. The summit’s system will be categorized into critical elements and assigned potential impacts (Stine et al., 2008). This step is documented in liaison with the system’s information security personnel.
Step 3: Assessment of provisional impact levels
Each part of the critical system’s provisional effect level will be reviewed depending on the critical system’s elements’ functions. The incidence response and management team will readjust the levels of an impact considering availability, integrity and confidentiality parameters, software development lifecycle levels, or organizational policies (Stine et al., 2008). The mission owners and other critical IT personnel will collaborate in generating a report on assessed impact levels.
Step 4: Assignment of system categories
After that, the incidence response team will identify security categorizations for information and the information system. This is attained by evaluating the possible impact levels concerning confidentiality, integrity, and availability (Stine et al., 2008). Depending on the security objectives, the team will adjust impact levels and conform to federal guidelines about assessment, approval, and reporting of all decisions.
Output: Security Categorization
The summit management entity will use the categorization as requirements and specifications for security measures in the risk management process.
Threats
Ransomware refers to a particular malware that encrypts files and services on systems and may erase data or hinder access to critical content, like in the nation’s summit. The ransomware is desi