Digital Forensic Examination of Counterfeit Documents
Introduction
A concerned citizen has contacted the police regarding the selling of counterfeit public documents. He told the police that he was going to the state residents to apply for a driver’s license. When he was almost reaching the office, he was approached by a man who told him he could create registration cards for vehicles at an affordable price to evade tax. Undercover officers met with the suspect, and after providing them with registration cards, he was arrested. A search warrant was obtained, and two computers from his home and a flash drive were seized. The investigator contacted the computer forensic laboratory to examine the evidence. Figure 1 below provides a snapshot of the investigation timeline and plan. Also, a budget in Appendix 1 was created and submitted to the Police Department for review. It was approved, and an investigation of the case began.
We will write acustom essay on your topictailored to your instructions!
187experts online
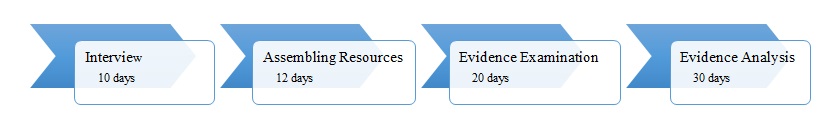
Figure 1: Investigation Timeline.
Interview Protocols
Before starting the interview process, the digital forensic examiner must first ensure that they are provided with the required legal documentation. These comprise verifying consent, search authority, warrant, and subpoena. These documents will help identify what legal level of analysis and the files that the examiner can examine. In this case, a copy of the evidence chain of custody and consent form may suffice, as in the appendix. To further compound the legal extent of the investigations, digital forensic examiners can review the case in regard to possible concerns related to the relevant Federal statutes (the Cable Communications Policy Act (CCPA) and the Electronic Communications Privacy Act of 1986 (ECPA), State statutes, and local laws and policies (United States Department of Justice, 2017). After the forms were reviewed and determined to align with the legal mandate, meetings were scheduled with the victim and case investor.
Case Investigator Meeting Agenda
Date: 5/4/2021.
Time: 11:00 AM – 1:00 PM.
Attendees: Case investigator and digital forensic examiner.
Meeting Objective
To determine the state of the crime scene and how evidence was collected.
Agenda
On-time delivery!
Get your 100% customized paperdone in as little as 1 hour
-
Review the documentation on the state of the crime scene (40 mins)
-
Review the victim’s allegations (40 mins)
-
Discuss possible investigative avenues regarding the type of evidence files sought (40 mins)
The following questions would be asked:
-
What was the location of the computers? Were they found powered on or off?
-
How were the computers collected?
-
What was the location USB thumb drive? What is found plugged in the processor?
-
How was the USB thumb drive collected?
-
Were there any copies of public documents retrieved from the crime scene, for instance, driving licenses?
Notes and Decisions
The two computer drives and USB thumb drive were collected and preserved appropriately. The picture of the crime scene is represented in Figure 2.

Figure 2: Overview picture of the crime scene.
-
There were no gaps in the victim’s statement
-
Digital forensic analysis should focus more on identifying graphic design files
Next Step
Deadline panic?
We're here to rescue and writea custom academic paperin just 1 hour!
Interview the victim to re-evaluate their statement.
Victim Meeting Agenda
Date: 5/7/2021.
Time: 11:00 AM – 12:00 NOON.
Attendees: Victim and digital forensic examiner.
Meeting Objective
To review the victim’s testimony. This would be achieved by creating a comfortable and calm environment for them throughout the interview. I would also t