A Study of Cyber Security Awareness of G12 CSS Students
Computer Science
How United Nations Children’s Fund (UNICEF)’s Mission and Vision Enable It to Contribute to Public Health and Safety Improvements
These encryption methods are used to protect WLANs from unauthorized access (Srikanth & Reddy, 2019). The Wi-Fi Protected Access (WPA) was first implemented in 2002 by Wi-Fi Alliance to eliminate network security issues experienced in WEP. Therefore, WPA came with MIC calculation for improved security (Srikanth & Reddy, 2019). Wi-Fi Protected Access 2 (WPA2), introduced in 2004, is an improvement of WPA. WPA2 protects information using CCMP protocol and for encryption. It is available in two versions; WPA2 – enterprise and WPA2 – personal. Wi-Fi Protected Access 3 (WPA3) was introduced in 2018, and it is an improvement of WAP2 (Srikanth & Reddy, 2019). It protects public networks efficiently because it eliminates brute force attacks, unlike in WPA2. Do you need urgent assignment help ? Reach out to us. We endeavor to assist you the best way possible.
Compare And Contrast Their Strengths and Weaknesses.
WPA, WPA2, and WPA3 encryption methods were developed in different years where a predecessor encryption method was succeeded by an improved encryption method (Srikanth & Reddy, 2019). Consequently, a successor encryption method offers better security features. WAP performs better than WEP, an earlier version of encryption, because it is compatible with most vendor devices. Also, WAP encrypts data better than WEP because of the MIC calculation feature. The 802.11 standards are well implemented in the WAP2 compared to WEP and WAP. WAP2 also uses CCMP to protect data from unauthorized persons.
CCMP encrypts and decrypts to ensure that man cannot access data in the middle when being transmitted. Only the receiver can have it decrypted at the destination. This is done using a pre-shared key and AES encryption. WAP3 has better encryption as compared to WAP2 – enterprise and WAP – personal. It protects data using Simultaneous Authentication of Equals as compared to WAP2’s Advanced Encryption Standard (Srikanth & Reddy, 2019). This improvement protects against the KRACK attack that was present in WAP2. Consequently, it is difficult to successfully perform a KRACK attack or brute force attack on a public network protected by WAP3. This is because an attacker cannot access old traffic from a network and decode it (Srikanth & Reddy, 2019). Devices that are not WAP3 enabled cannot access a WAP3 protected network connection. This is efficient in ensuring that the network is secure.
WAP3 Preference
Using the WAP3 encryption method would be prudent because it offers the strongest protection against network attacks (Srikanth & Reddy, 2019). According to Bartoli (2020), it is evident that using an encryption method lower than WAP3 would expose the network to attackers. The experiments illustrated remote connections to a server using WAP, WAP2, and WAP3 and the vulnerabilities that would be experienced in the three encryption methods. In WAP and WAP2 encryptions, it was possible for unauthorized persons to access data. However, in WAP3, no data could be obtained illegally. The only notable challenge in WAP3 was that connection authorization failed for some devices that were not WAP3 compatible (Bartoli, 2020). The Simultaneous Authentication of Equals is efficient in implementing WAP3 encryption. This would be used together with other standards based on the security needs of a network. For example, 802.1x could be used with 196-bit security to fully protect a network. 802.11s standard could also be employed as it checks on mesh network security. The Simultaneous Authentication of Equals ensures that all legal peer devices on a network are identified to avoid attackers from gaining access (Srikanth & Reddy, 2019). Therefore, the 802.11s would work well with SAE.
References
Bartoli, A. (2020). Understanding Server Authentication in WPA3 Enterprise. Applied Sciences, 10(7879), 2-12. https://www.mdpi.com/2076-3417/10/21/7879/pdf
Why might the development and morphing of roles based on gaps in medicine be problematic for advancement of APRNs? What actions might a nurse take to reduce this?
In what ways can an APRN distinguish his or her role from other nursing roles and medical counterparts? Why might this be important?
How can APRNs encourage nursing-based outcome studies?
Expectations
We’ll write everything from scratch
Question 
Each student nurse will work with a partner (“the patient”) to complete a health history interview using Gordon’s Functional Health Patterns to document a narrative overview of the patient’s health.

Health History Interview- Using Gordon’s Functional Health Patterns
The “patient” will be free to use their own personal information or may answer the questions in the interview acting as someone else (the “patient” does not need to disclose if the information is real or is part of acting as a patient). Students will follow the Functional Health Pattern Rubric, along with text or online resources for Gordon’s Functional Health Patterns and Erikson’s stages of development, to complete the assignment.
For Internet information systems developers, there are many programming and development options for building a mobile app. As part of the analysis and design process for your project with Healthy Harvest, you need to determine how to approach the technical build by researching and comparing the technology available. Python, JavaScript, Java, Scala, and Ruby are just a handful of the programming languages used, and as an IS consultant, you must narrow down the viable options.
Internet Systems Technologies Comparison
Create a 3- to 4-page document or spreadsheet to compare specifications, pros, and cons of 5 systems development tools. Complete the following:
Research and identify 5 systems development tools suitable to develop the Healthy Harvest online store.
Compare 10 to 12 specifications and features of each tool that can support Healthy Harvest’s online store.
Write a 1-page summary that explains how these technologies can bring value to Healthy Harvest.
Tips for completing this assignment:
Review the grading rubric to begin organizing your assignment. It clearly defines expectations and is what your faculty member will use to grade your submission.
Apply the knowledge and skills you have learned in this course.
Use the knowledge and skills you have learned in prior courses.
Ask your faculty member any questions you may have.
Cite any references to support your assignment.
Format your citations according to APA guidelines.
Strategies that Might be Effective in Reducing or Resolving Conflicts Between Police and Communities
Conflict and Power Between Law Enforcement and Citizens
Factors or Conditions that Contribute to Conflict Situations Between Law Enforcement and Citizens
Discussion Prompt
Part 1:
Choose a condition from the following case studies (Week 4 Case Studies). You may work in small groups of up to 3 students if desired.
Case Study 1- Otitis Media
Part 2: Answer the following questions
Discuss what are the potential treatments for this child’s diagnosis
What antibiotic/s should be given for this patient’s diagnosis?
How long should you prescribe the chosen antibiotic?
What teaching would you give this child’s parents on the prescription?
Write out a correct prescription for the antibiotic you are going to prescribe for this patient. (Be sure to include all elements needed for a correct prescription)
Expectations
Initial Post:
Length: A minimum of 500 words, max of 1000, not including references or attachments
Citations: At least one high-level scholarly reference in APA from within the last 5 years
Developing a Searchable PICO(T) Question for Clinical Inquiry
Responding to Kimberly
Risk Assessment Report
Risk assessment is the process conducted by an organization to identify and analyze the risks that are likely to occur in the organization. The identification and analysis of risks help organizations to implement measures that can help mitigate the risks. There are different steps involved in the risk assessment process. The initial step involves the identification of possible threats likely to affect the organization. The next stage includes noting the possible targets of the identified risks. Possible targets can include network users or even network resources. The organization then proceeds to rate the different identified risks according to their possibility of occurring and their impact in case they occur. Different mitigation measures are then developed and implemented, beginning with the highly prioritized risks. The different fields that makeup risk assessment in an organization include risk analysis, risk mitigation, and risk management (Anikin, 2015).
By Day 1 of this week, you will be assigned to a specific case study for this Case Study Assignment. Please see the “Announcements” section of the classroom for your assignment from your Instructor.
The Assignment
Develop a 1- to 2-page case study analysis in which you:
Explain why you think the patient presented the symptoms described.
Identify the genes that may be associated with the development of the disease.
Explain the process of immunosuppression and the effect it has on body systems.

Case Study Analysis of 24-year-old male with Dandruff Pitted Fingernails and Morning Joint Pain
Scenario: A 24-year-old male presents to the clinic with a chief complaint of developing large areas of dandruff to his scalp and pitting of his fingernails. He also started noticing that he is having morning joint pain that is partially relieved after he gets ready for work. He has used multiple types of dandruff shampoo without relief of symptoms. He is unable to remember any significant family history concerns. Labs include a rheumatoid factor which was negative. His ESR was mildly elevated.
Develop a 1- to 2-page (not including Introduction & Conclusion) case study analysis in which you:
Explain why you think the patient presented the symptoms described.
Identify the genes that may be associated with the development of the disease.
Course Reflection – Enhancing Nursing Practice Through Multidimensional Care for Diverse Patients
Apply Strategies for Safe, Effective Multidimensional Nursing Practice When Providing Care for Clients with Neurological Disorders.
Project 2: Introduction to Packet Capture and Intrusion Detection/Prevention Systems
Network traffic analysis and monitoring help distinguish legitimate traffic from malicious traffic.

Joint Network Defense Bulletin
Network administrators must protect networks from intrusions. This can be done using tools and techniques that use past traffic data to determine what should be allowed and what should be blocked. In the face of constantly evolving threats to networks, network administrators must ensure their intrusion detection and prevention systems are able to analyze, monitor, and even prevent these advanced threats.
In this project, you will research network intrusion and prevention systems and understand their use in a network environment. You will also use monitoring and analysis technologies in the Workspace to compile a Malicious Network Activity Report for financial institutions and a Joint Network Defense Bulletin for a financial services consortium.
The following are the deliverables for this project:
Deliverables
- Malicious Network Activity Report: An eight- to 10-page double-spaced Word document with citations in APA format. The page count does not include figures, diagrams, tables, or citations.
- Joint Network Defense Bulletin: A one- to two-page double-spaced document.
Step 1: Create a Network Architecture Overview
As part of your assignment to report on prevention methods and remediation techniques for the banking industry, you would have to travel to the various bank locations and gain access to their networks. However, you must first understand the network architecture of these banks.
Provide a network architecture overview along with diagrams. Your overview can be fictitious or based on an actual organization. The goal is to provide an understanding of the network architecture.
Describe the various data transmission components. Select the links below to review them:
- User Datagram Protocol (UDP)
- Transmission Control Protocol/Internet Protocol (TCP/IP)
- internet packets
- IP address schemes
- well-known ports and applications
Address the meaning and relevance of information, such as:
- the sender or source that transmits a message
- the encoder used to code messages
- the medium or channel that carries the message
- the decoding mechanisms used
- the receiver or destination of the messages
Describe the digital investigation or security certification you would choose to supplement your education best and support your career plans. Why did you choose this one?
Instructions
Write a one-page reflection in which you consider your journey from the beginning of this term to the end.
Describe how your interactions with your fellow learners in the residency course you are taking simultaneously have helped you understand the challenges of being a doctoral learner.
Describe your perceptions of how the remainder of your doctoral journey will progress.

Peer Engagement in Doctoral Residency- Unveiling the Challenges and Insights of Doctoral Learners
Explain how you might reach out to other learners or faculty for assistance when needed.
Finally, provide any thoughts on improvements to the Quarter 1 process in your DIT program.
Submission Requirements
Written communication: Write in a professional manner using current APA style and formatting with correct grammar, usage, and mechanics.
Resources: None required.
APA formatting: Format and cite any optional resources used according to current APA style and formatting
For Internet information systems developers, there are many programming and development options for building a mobile app. As part of the analysis and design process for your project with Healthy Harvest, you need to determine how to approach the technical build by researching and comparing the technology available. Python, JavaScript, Java, Scala, and Ruby are just a handful of the programming languages used, and as an IS consultant, you must narrow down the viable options.
Internet Systems Technologies Comparison
Create a 3- to 4-page document or spreadsheet to compare specifications, pros, and cons of 5 systems development tools. Complete the following:
Research and identify 5 systems development tools suitable to develop the Healthy Harvest online store.
Compare 10 to 12 specifications and features of each tool that can support Healthy Harvest’s online store.
Write a 1-page summary that explains how these technologies can bring value to Healthy Harvest.
Tips for completing this assignment:
Review the grading rubric to begin organizing your assignment. It clearly defines expectations and is what your faculty member will use to grade your submission.
Apply the knowledge and skills you have learned in this course.
Use the knowledge and skills you have learned in prior courses.
Ask your faculty member any questions you may have.
Cite any references to support your assignment.
Format your citations according to APA guidelines.
Question 
The topic for this module week is privacy and security. As we can expect, there are challenges in maintaining secure devices as consumers as well as providing a secure network as a service provider. This provider could be the local coffee shop or a multi-million dollar aircraft. One area of interest is the In-Flight Entertainment (IFE) systems on these aircraft, which may be connected to the same network as the navigation and control systems. Let’s look at an IFE testing process in a modern plane by watching this video.

Privacy and Security
Pushing 787 In-flight Entertainment System to the Limit (YouTube – 2:27) (Links to an external site.)
In addition to the onboard IFE, passengers also carry with them an array of personal electronics: smartphones, tablets, laptops, gaming devices, etc. So, today’s travelers may well be using electronics almost from gate to gate.
One might ask, with travelers bringing with them so many devices on board (BYOD), what changes are we seeing with IFE systems? To answer that, here is an excerpt on IFE from an airline market business analysis (Cision PR Newswire (Links to an external site.)):
Key airlines across the globe are replacing heavy cablings and screens with onboard Wi-Fi systems for passengers to accommodate the BYOD model, thereby reducing the overall weight of the aircraft.
There has been an increasing trend of passengers bringing their Personal Electronic Devices (PED) on board and willing to pay an additional fee for using Wi-Fi during the flight.
Moreover, there is an upsurge in demand for streaming live TV onboard directly on the passengers’ devices, ultimately creating lucrative growth opportunities for the in-flight entertainment and connectivity (IFEC) market.
We’ll write everything from scratch
Question 
Encryption Methods
In a minimum 2-page paper, review encryption methods WPA, WPA2, and WPA3. Compare and contrast their strengths and weaknesses. Then, explain which version you would use and why. Would you include any authentication mechanisms, such as 802.1x or similar?
Based on the research you do and any leadership experience you may have, compose a minimum 2-page, double-spaced research paper using the current APA version with a title page and reference page.
Given today’s work environment, particularly with professions dealing with data governance, discuss how a leader’s planning and prioritization can help achieve data security and protect privacy using a data governance plan. What leadership roles and responsibilities are most important for planning and priorities in data governance? How do you decide what is a higher priority for data security and privacy? What level of support is needed for successful data governance, and how do planning and prioritization help achieve that?
Instructions
Write a one-page reflection in which you consider your journey from the beginning of this term to the end.
Describe how your interactions with your fellow learners in the residency course you are taking simultaneously have helped you understand the challenges of being a doctoral learner.
Describe your perceptions of how the remainder of your doctoral journey will progress.

Peer Engagement in Doctoral Residency- Unveiling the Challenges and Insights of Doctoral Learners
Explain how you might reach out to other learners or faculty for assistance when needed.
Finally, provide any thoughts on improvements to the Quarter 1 process in your DIT program.
Submission Requirements
Written communication: Write in a professional manner using current APA style and formatting with correct grammar, usage, and mechanics.
Resources: None required.
APA formatting: Format and cite any optional resources used according to current APA style and formatting
Target Scoping and Network Exploitation
Part 1: The Five Elements of Target Scoping
Network Vulnerability Assessment – Metasploit
Program Development
Implications of Using ZIP Codes on the 1NF, 2NF, and 3NF Rules
The use of different data types and databases is commonplace in program development. Relational databases are data sets with predefined relationships, and a change in one data element can affect other data. The first nominal field (1NF) in relational databases implies that the area can only contain one predefined data type or an atomic value. On the other hand, the second nominal form (2NF) is when the data field follows 1NF rules but has other variables entirely dependent on the primary key. 3NF, the third little form in relational databases, arranges data in a series following the 2NF principle without dependency (Link & Prade, 2019). The relational database containing addresses for each data field implies that the database will use a string for the atomic value, which can be used in the first nominal form for the lesson. The address string can be the primary key to link the other data variables in the second little form (Link & Prade, 2019).
Program Development
Implications of Using ZIP Codes on the 1NF, 2NF, and 3NF Rules
The use of different data types and databases is commonplace in program development. Relational databases are data sets with predefined relationships, and a change in one data element can affect other data. The first nominal field (1NF) in relational databases implies that the area can only contain one predefined data type or an atomic value. On the other hand, the second nominal form (2NF) is when the data field follows 1NF rules but has other variables entirely dependent on the primary key. 3NF, the third little form in relational databases, arranges data in a series following the 2NF principle without dependency (Link & Prade, 2019). The relational database containing addresses for each data field implies that the database will use a string for the atomic value, which can be used in the first nominal form for the lesson. The address string can be the primary key to link the other data variables in the second little form (Link & Prade, 2019).
Server Virtualization and Cloud Computing
In the contemporary world of globalization and enterprise technologies, cloud computing and server virtualization are technologies that play an essential part in enhancing how organizations work. Organizations that intend to succeed in any industry must embrace technology or risk being left behind and losing their market share to more technologically advanced competitors. Virtualization is a form of technology where a copy or virtual instance of a real-life object or technology is used instead of the actual. This technology utilizes both software and hardware resources to make work easier (Zhang, 2018).
Webstore Implementation and Maintenance Plan
Recommended Strategy for Phases of Implementation
Integration:
Module integration in software development is done after successful integration testing (Noortaj, 2019). It is good practice to develop different modules independently and then integrate them. This enables software developers to focus on the function of each module before integrating them into one system. For example, the Healthy Harvest Online Store App would have several modules. These would include a login module, a cart module, a payment module, etcetera. Each module would be developed separately and tested before being integrated as one application. This would ensure that the modules work as expected and that there would be no errors and bugs introduced into the app after integration. Also, debugging modules independently is easier and faster than debugging an already integrated system. Another aspect of integration in the Healthy Harvest Online Store App would be when the app is connected to an external system. For example, the app could be integrated with an online payment platform that allows customers to make electronic payments for the groceries they order. Integration of the app with an external system would only be done after the app is tested and approved for live operations. Do you need urgent assignment help ?
Testing:
Question 
Methods of Ensuring Business Continuity and Disaster Recovery
Section 2: Using FTP/tftp, SNMP and QoS
Write a minimum 1-page paper on how best to use FTP/TFTP, SNMP, and QoS to improve business continuity and disaster recovery, including tools, personnel, training needed, etc.
c) What are some challenges to ensuring everyone in an organization follows the cybersecurity policy?
Part 2: Cybersecurity Policy Foundation-Overview
In a minimum of 1,250 words, answer the following question:
1) Why does an organization’s management present unique challenges regarding policy compliance? Provide examples.
Part 3: Access Controls
In a minimum of 1,250 words, answer the following:
1) Evaluate the different types of access controls and their roles in a “defense-in-depth” strategy.
NB: Your submission should:
Include a cover sheet.
Be double-spaced.
Be typed in Times New Roman, 12-point font.
include correct citations
be written in Standard English with no spelling or punctuation errors; and
have at least eight accurate references at the bottom of the last page.
Access Controls and Security Technologies
Part 1: Cybersecurity Policy Review
Role of Cybersecurity Policy
Cybersecurity policy has multifaceted functions in securing public organizations, private organizations, government organizations, and the nation’s infrastructure. The cybersecurity policy guarantees the proper assignment of roles and responsibilities among information system experts. (Lubua & Pretorius 2019; Kahyaoglu & Caliyurt, 2018). This approach ascertains that each party accounts for events within their jurisdiction area. Baleva (2021) explains that cybersecurity professionals perform some of these roles, including threat intelligence, maintaining network safety, safeguarding data files, and managing vulnerabilities.
Cybersecurity Operations and Administration
A policy can be described as a statement that describes the acceptable behaviour, goals, and ethics of a particular organization or enterprise. Policies are used to guide organization members to ensure the organization is moving in one direction towards achieving its objectives. Cyber security and security generally cannot be controlled by one person or department but rather depend on the entire organization’s behaviour. Security policies cannot solve these problems, but if properly written and followed by the organization’s members, they can drastically reduce attack risk (Sehgal, Bhatt & Acken, 2020).
Peer-to-Peer Networks
Peer-to-peer networks provide various benefits, such as increasing the ease of sharing files between users, providing fault tolerance in a network, and addressing the issue of censorship in the network. Despite the various benefits of peer-to-peer networks, they also present challenges that raise ethical and moral dilemmas. An example of an ethical issue raised by peer-to-peer networks includes the unrestricted sharing of copyrighted files (Christin, 2011). Apart from sharing copyrighted files, the issue of sharing illegal files is associated with peer-to-peer networks. Various aspects have to be considered to determine whether peer-to-peer networks are fundamentally right or wrong. These aspects include the end-users, the content providers, and Internet Service Providers (ISPs). From the end-users perspectives, peer-to-peer networks provide an opportunity to access the content they require by paying the least possible charge. While content providers note the loss of revenue from the presence of peer-to-peer networks, changes in their business models can address copyright infringement issues (Christin, 2011).
For any organization to settle on an appropriate encryption technique, it should be able to tell apart these three data states. The first state of data is data at rest, which involves data stored on devices operating on a particular network. Since this data type is mostly preserved, it has been identified as less risky than data in motion. In this regard, data at rest may include information saved in a database or on a portable device (Ghouse et al., 2019). Secondly, the data in use denotes data actively accessed and processed by the users. Data in this state has been identified as the most vulnerable, irrespective of whether it’s being read, processed, or updated, because of its ease of accessibility (Ghouse et al., 2019). In this stage, the data is regularly exposed to external attacks or becomes vulnerable to human mistakes that may yield serious implications. Get in touch with us at eminencepapers.com. We offer assignment help with high professionalism.
Public Service Announcement on Cyber Espionage
In modern times, every business can be a target of cyber espionage. No matter the size or sector a company is in, they are at risk. Cyber espionage is such a significant threat, and this public service announcement aims to raise awareness about it. The goal is to give organizational leaders some insights on how to protect their systems and data from attacks. This announcement will address three common threats that companies face, provide countermeasures for them, and outline the steps needed if the system ever gets compromised.
Write a paper in which you include the following:
Introduction.
IT Business Problem.
Choose one of the articles and discuss the noted IT business problem.
Cite at least two additional sources that discuss this problem.

Analysis of Research Methods and Theories
Theories, Concepts, Methods.
Describe and define any theory or conceptual/theoretical framework discussed in the article.
Describe the methodology and research approach used in the article and explain how you might use it if you decide to research a similar problem.
Scholarly Research.
Explain how that theory or conceptual/theoretical framework is used to guide the research.
Describe which data were analyzed in the research.
Conclusion.
Conclude by explaining how this assignment helped you understand how theory can help guide a researcher in determining their research method. Provide insights into how you have begun considering research problems and topics. If you have an idea about a business technical problem, explain it briefly here; if you have not yet considered a business technical problem, explain your next steps as to how you might identify one. What help from cohort members, coworkers, business association members, friends, family, or others have you enlisted or plan to request?
Question 
Post a two-paragraph posting in which you do the following:
Read the attached snippets taken from the DIT/DBA Dissertation Chapter Guides. (pdf) Then, do the following.
Describe briefly a topic that you have considered for use as your topic in this program and explain why.

Smart Watch in the Medical Field
Discuss, briefly, one or two articles you found through online research or in the Capella Library that discuss the topics that interest you. Cite those articles using APA style and formatting.
Virtualization began in the 1960s as a method for logically dividing the system resources provided by mainframe computers between different applications. Since then, the meaning of the term has broadened. Today, virtualization refers to the ability to create multiple independent instances of servers and desktops with disparate operating systems running on a single physical computer.
Security Benefits and Challenges of Virtualization in a Cybersecurity Context
Research and write a 600-word report discussing virtualization and properly using the vocabulary associated with cybersecurity.
Address the following:
Describe the fundamental concepts of the cybersecurity discipline and use them to provide system security.
Describe the main components of confidentiality, integrity, availability, access, authentication, authorization, nonrepudiation, and privacy.
Define and contrast the terms host and guest operating system.
Define the term hypervisor.
Compare and contrast the different types of hypervisors, how they are used, and the advantages and disadvantages of each.
Discuss the advantages and disadvantages of a virtualized computing environment.
Describe how virtualization can assist a cybersecurity analyst in exploring malware and explain how you would examine attack indicators and attack timing.
Support your report with at least 3 scholarly resources.
Cybersecurity is a fast-evolving field that is continually being faced with new challenges for not only individuals but also companies and government agencies. Even though a great population of current users understands cybersecurity as a discipline concerned with protecting computers from viruses and other forms of malware, this is only one aspect of this noble subject (Corallo et al., 2020).
Prepare audits and investigations of electronic computing devices.
Network and System Monitoring Analysis
Using the class materials, the Library, and Internet resources, research the topics involved and provide a complete response to the following:
- Explain three possible uses of a SPAN port that you might use as a forensic investigator.
- Explain two disadvantages of a SPAN port you might encounter as a forensic investigator.
- Wireshark supports two types of filters. Research, and in a whole paragraph for each, address the following:
- Explain each and when you might use each.
- Describe three non-Ethernet protocols Wireshark can capture.
- Many brute force programs will use dictionary words. Describe how you will decide which words to put in a dictionary to be used in a program like Bruter.
The two broad categories of encryption are symmetric and asymmetric encryption. Symmetric encryption is a strategy that utilizes the secret key, which in most cases can either be a word, a number, or a string of random letters. This strategy encompasses blending with the plain text of the message to change the content in a certain way. The secret key used in encrypting the message should be known by both the sender and recipient for encryption and decryption processes to occur seamlessly. Examples of symmetric encryption include DES, RC5, RC6, and AES (Dixit et al., 2018, p. 241).
Wireless Network Attacks
Part 1: Wireless Hacking
Tools Used by Black Hackers to Attack Wireless Traffic
Risk Management and Compliance concerning Cybersecurity Policy and Industry Standards
Part 1
Risk Management Framework
Question 
Assessment Description
From the attached Word document “Research Paper”, Identify your research question. Refine it from your original question, if needed, based on the research you have completed.
Create an Annotated Bibliography from the 10 references used in your Reference List assignment. Be sure to include an APA-style reference for each article. Each annotation must be 120 words in length and include the following elements:

Enhancing Natural Language Processing in Virtual Assistants through Transformer Models
Each reference includes an annotation that addresses the following:
1. Paraphrased summary of the article
2. Why it is considered a scholarly reference
3. Reflection on how it is applicable to your research
Note on Paraphrasing: Paraphrasing the ideas of others is a requirement in academic writing and graduate study. Paraphrasing is using your own words to restate ideas or information from source material. As you write each annotation, use these three main steps to paraphrase:
1. Identify the original idea(s) in the article.
2. Identify general points regarding the idea(s).
3. Summarize the general points of the article in your own words.
Advancements in Natural Language Processing (NLP) and Artificial Intelligence (AI) have helped attain a meaningful transformation in how people interact with machines. Natural language processing enables the communication between computers and human language (Bharatiya, 2023). Powering NLP algorithms with virtual assistants enhances multiple domains, including mobile data mining and IoT voice interactions.
Advancements in Natural Language Processing (NLP) and Artificial Intelligence (AI) have helped attain a meaningful transformation in how people interact with machines. Natural language processing enables the communication between computers and human language (Bharatiya, 2023). Powering NLP algorithms with virtual assistants enhances multiple domains, including mobile data mining and IoT voice interactions.
The Effectiveness of a PowerPoint Presentation
TOPIC: Consider your current or future career, clubs volunteer activities, or any other occupations where a PowerPoint presentation might be advantageous. Where might you use PowerPoint? Could the skill of making a professional presentation mean the difference between success and failure? Please describe specific scenarios for each occupation.
What products or people are known for the way that they are presented? Why? How can an effective presentation enhance a message? How can the wrong image confuse or distort a person’s message? Again, please give specific examples. Do not generalize.
Digital Forensic Compilation Report-Out

Digital Forensic Compilation Report-Out
In this step, your team’s digital forensic investigator will collaborate to create a Compilation Report-Out of at least 20 pages on the information and data gathered through the projects and steps of this course.
Use the attached lab reports to come to complete this assignment.
Question 
Instructions
Submit a one page outline with your proposed term paper title, thesis statement, and an outline of the subtopics you will cover in your paper. The term paper details are listed below. ALL TOPICS MUST BE APPROVED. A FAILURE TO HAVE THE TOPIC APPROVED WILL RESULT IN A ZERO GRADE FOR THE TERM PAPER OUTLINE AND THE TERM PAPER. You can send a message with the topic for approval.

Term Paper Outline
This project provides you with the opportunity to increase and demonstrate your understanding of cyberlaw theory and practice. You will need to choose a law(s) that you are interested in researching. The paper must be 2-3 pages in length detailing the below questions. Before completing the below steps, please make sure that the topic is approved.
1. Thesis: What law are you researching (You are to choose a specific law. Please do not choose a topic)? What position do you want to take in regard to your chosen law? You will need to decide if you agree or disagree with the current way the law is written. You can choose to like certain aspects of the law and not others.
2. Background: What is the existing point you want to challenge or support, and how did the law get to be that way (This is where you would need to find cases, background information, etc.)?
3. Inadequacies: What are the deficiencies in the present way of doing things, or what are the weaknesses in the argument you are attacking?
4. Adequacies: Discuss the positive aspects of the law?
Description
This study aims to investigate the possibility of improving Natural Language Processing (NLP) skills in virtual assistants by using Transformer models. Virtual assistants are becoming more common in various fields, including smart homes, IoT voice interactions, mobile data mining, and healthcare (Kang et al., 2020). However, existing NLP techniques employed in virtual assistants frequently need help interpreting user goals and fully handling complicated inquiries. Vaswani et al. (2017) unveiled the Transformer model that changed NLP tasks with its attention mechanism and parallel processing capabilities. This study looks at how adopting Transformer-based methodologies might improve the performance, efficiency, and user experience of virtual assistants in various applications.
Description
This study aims to investigate the possibility of improving Natural Language Processing (NLP) skills in virtual assistants by using Transformer models. Virtual assistants are becoming more common in various fields, including smart homes, IoT voice interactions, mobile data mining, and healthcare (Kang et al., 2020). However, existing NLP techniques employed in virtual assistants frequently need help interpreting user goals and fully handling complicated inquiries. Vaswani et al. (2017) unveiled the Transformer model that changed NLP tasks with its attention mechanism and parallel processing capabilities. This study looks at how adopting Transformer-based methodologies might improve the performance, efficiency, and user experience of virtual assistants in various applications.
We’ll write everything from scratch
Question 
How Can We Ensure Our Data And Codes Are Accurate In Our Research?
About my last discussion that you did, can you answer this question?
Shajaira, thanks for sharing these two research studies with the class. You made some excellent points. Errors in data collection or coding can play a significant role in the outcomes of a survey. This is important to know, as coding can be very complicated. If data collection errors occur, the results will not be accurate. How can we ensure that our research data and codes are correct?
Cybersecurity Policies without Borders
Cyberspace and Cybersecurity Law Makers
Cybersecurity is how persons, organizations, or bodies work towards reducing cyber attacks by protecting data and programs from being damaged, stolen, or attacked by spammers or hackers. Several bodies provide cyber security laws, including the federal and state governments.
Various laws apply once cybercrime crosses national and international boundaries. The first law is known as the Convention on Cybercrime Law. This law applies to international borders because it protects computer systems’ integrity by criminalizing unauthorized access to systems using various techniques. This law grants countries the right to develop laws in their domestic jurisdiction to prevent unauthorized access to part of the system by third parties without the right to do so (Siregar & Sinaga, 2021).
Question 
Analyzing Computer Programs
Overview:
In this assignment, you will be analyzing simple program logic, the structure of a modular program, creating hierarchy charts, and feature of good program design.
Instructions:
Part I
- Research:
- Early programming using low-level machine languages. Explain what these languages looked like and what types of problems were encountered when using them.
- Object-oriented programming techniques. Describe the advantages and disadvantages of using object-oriented techniques.
Part II
- 1. Create either pseudocode or a flowchart for a program that does the following:
- a) Prompt the user to enter a sales tax rate.
- b) Prompt the user to enter a price.

Analyzing Computer Programs
- c) Calculate and output the amount of tax for the item and the total price with tax.
- 2. Create either pseudocode or a flowchart for a program that does the following:
- a) Prompt the user to enter two times of day in HH:MM format, and then calculate and print the difference between those two times in minutes.
- 3. Create either pseudocode or a flowchart for a program that does the following:
- a) Prompt the user to enter his or her birthdate: year, month, and day.
- b) Calculate the number of days old the user is. (You can decide to include or ignore leap years.)
- c) Modify the program to include the number of hours old the user is.
- d) Modify the program to include the number of minutes old the user is.
- e) Modify the program to include the number of seconds old the user is.
Question 
Digital Forensic Application
For this assignment, you will explore your possible future role in this field by researching employment prospects for computer forensics investigators. Compose an essay on this topic. In your essay, be sure to include the following components.
• Explain the importance of computer forensics.
• Describe why the need for computer forensic examiners will be in demand over the coming years. Include statistics detailing the growth of certain cybercrimes.
• Explain the skills, training, and education required to become a computer forensics investigator.
Your essay must be at least two pages long and use two academic sources. You should also include an introduction and conclusion section in your essay. Adhere to APA Style when creating citations and references for this assignment. APA formatting, however, is not necessary.
We’ll write everything from scratch
Question 
The Personal Cloud Storage Database
TOPIC: Describe a database that might be used in your current or future career. Using this data, explain the relationship between a field, a record, a table and a database. In addition, what are the advantages of managing database information in Access versus using a worksheet in Excel?
We’ll write everything from scratch
Question 
Database Concepts – eCommerce Database
Describe a database that might be used in your current or future career. Using this data, explain the relationship between a field, a record, a table and a database. In addition, what are the advantages of managing database information in access versus using a worksheet in Excel?
We’ll write everything from scratch
Question 
Discussion – Excel Uses
In what career paths would knowledge of excel worksheet benefit an individual? I would knowledge of excel be beneficial for you in your current or future career? How could you use excel in your personal life? (please consider any volunteer activities, clubs,
Three of the Most Promising Websites and Their Use in Forensic Examination
Research Paper – Audio/Video System
Overview:
In this assignment, you will write about a hardware system configuration with technical specificity and research references.

Hardware System Configuration
Instructions:
You have decided that you can make good money being a YouTube sensation. You have a talent (pick one you have or make one up), and you want to create a YouTube channel with audio/video content to attract viewers. Since this will be your business, you do not want any of your personal computers to be involved, and you need to buy all the components to support your production.
- At a minimum, research and select these components to build your YouTube business system:
- System unit (specifically describe the CPU and RAM choices you made, and why) o Top-of-the-line video card (no on-board video for you)
- Minimum 4K 32″ monitor
- External microphone (include an audio preamp/compressor)
- External camera
- Lighting
- Operating system
- Storage choices to back up your video library
- Explain what was important in making each decision about all the hardware and external devices and why you settled for the system build you chose.
- Explain the value of the choices and how much the system will cost.
- Describe all the peripheral device connectors to ensure that they all work together (or include adapters, where needed).
- Cite every component separately, with a website reference that lists all the technical specifications of the component. Use the APA style where images are included in appendices so that your finished paper contains images of each component in one or more appendix and referenced in the paper (for example, “The monitor will be an X
Describe all the peripheral device connectors to ensure that they all work together (or include adapters, where needed).
Explain what was important in making each decision about all the hardware and external devices and why you settled for the system build you chose.
Ratios and Proportions
In Mathematics, a proportion is a statement of equality between two ratios. Balances can be solved using various methods, including cross-multiplication and setting up a balance using equivalent fractions (Billstein, Libeskind & Lott, 2013). Cross multiplication refers to multiplying the numerator of one bit by the denominator of the other and vice versa. Additionally, this can be done to create an equation that can be solved for a missing value. First, to set up a proportion using equivalent fractions, find two ratios that are equal to each other. Then, set up an equation using these ratios and solve for the missing value.
Cryptographic Hash Function Reflection
Definition of Cryptographic Hash Functions
Cryptographic Hash Function (CHF) is an equation or algorithm that maps a particular data set into a hash value (Wang et al., 2017). It can simply be defined as a mathematical function that derives a special string of texts from any form of arbitrary data. The hash value, in this case, refers to the produced enciphered text and is mostly of fixed size. Such converted plaintexts are usually fitted into complex data structures or tables that literary holds fixed-size elements. The generated structures/tables are termed the hash tables and are deemed to be secure. CHF tends to be mistaken for encryption, but the main difference is that it is a one-way function, unlike the latter, which can be deciphered using a unique key. There are several hash functions, including secure hashing algorithm 1 and secure hashing algorithm 256.
Cryptographic Hash Function Reflection
Definition of Cryptographic Hash Functions
Cryptographic Hash Function (CHF) is an equation or algorithm that maps a particular data set into a hash value (Wang et al., 2017). It can simply be defined as a mathematical function that derives a special string of texts from any form of arbitrary data. The hash value, in this case, refers to the produced enciphered text and is mostly of fixed size. Such converted plaintexts are usually fitted into complex data structures or tables that literary holds fixed-size elements. The generated structures/tables are termed the hash tables and are deemed to be secure. CHF tends to be mistaken for encryption, but the main difference is that it is a one-way function, unlike the latter, which can be deciphered using a unique key. There are several hash functions, including secure hashing algorithm 1 and secure hashing algorithm 256.
Understanding Computer Hardware and Components
Hardware is defined as the physical components that are needed for a computer system to function, there are internal hardware components such as the motherboard whereas an external hardware feature or a peripheral could be a mouse. Do you need help with your assignment ?
Based on (Goodman, 2021), the Motherboard is the main printed circuit board of a computer; it contains the CPU, and it distributes power to other components and facilitates their coordination.
The Pepsi website contains information about the company’s products. This includes the different flavors of soft drinks, calories in each, and other nutritional information (Pepsi, 2021). Such information is important as it enables customers to choose a suitable drink. The information is displayed using graphics. Meaning each product is illustrated in graphics. Therefore, customers can easily relate a physical can of soft drinks in the shop with the one on the website. According to Daher (2019), infographics showcase data as well as information using graphics. This means that the Pepsi website is an infographics website.
Discussion – Solutions for Computer Science Problems
The Problems
The development of solutions for computer science problems is limited by several challenges with different impacts. Programmers work in the best interest of a project and look forward to ascertaining all components work as intended. However, errors may end up inhibiting the project, leading to the need to debug. This is a momentous crisis, and its outcomes are profoundly felt when there are excess bugs. For instance, some buttons might fail to work, missing commands, and other functional errors. Debugging frustrates new developers and delays the project; hence, it is considered a significant problem (Coker et al., 2019).
Scoping Data Questions Using the CONVO Framework
The CoNVO framework includes context, need, vision, and outcome that facilitates success in a data project (Shopenova, 2021). The context describes the background to be addressed in the project, while the need describes the challenges that are to be handled (Foong, 2020). The vision outlines the solution to be built, and the outcome details what is to be achieved by the project for it to be considered a successful project (Foong, 2020).
t Controversy – Fake News
Fake news, also considered disinformation, spreads faster in society today because of the presence of the internet and social bots. This phenomenon is responsible for the rise in cases of people committing suicide over false allegations made about them, consumers refusing to purchase products from a legitimate company, and political unrest in countries. For instance, in 2016, the United States ‘ population was nearly influenced not to elect their former president because of the fake news spread about Russia’s intervention in their election processes. Today, disinformation has hurt more than it merely compels a difference in views in the consumer. Fake news spread over the internet impacts its consumers negatively and associated accused persons,
What are 3 ways to track an offender? Give an example of each.
What types of tools are used in the process of a digital or network investigation?
What information can be learned through these tools about intrusion or other cybercrime?
What are the main investigative tools that all cyber crime investigators should have? What are some of the specialty tools that investigators would require for specific types of investigation such as network intrusion or mobile investigation?
Analysis and Recommendations on Dashboard Design Principles
Dashboard Design
Why is it recommended not to exceed the boundaries of a single screen?
Analysis and Recommendations on Dashboard Design Principles
Dashboard Design
Why is it recommended not to exceed the boundaries of a single screen?
Preparing Summarizing and Describing Data
Cardello Lighting and Electric retailer is an independently owned company and has been operational for over 70 years. It supplies genuine commercial and residential electrical supplies to empower the surrounding community. The firm has a wide array of indispensable data that will be of great relevance in this context. The data is typically centred on electrical accessories, including ceiling lights, lamps, and home cinemas, among other electrical portfolios (CLES, 2021). Its grain data is expansive and features inventories taken each week for specific products, detailed transactions for clients as processed by the sales scanner, weekly average profits and losses, a record of daily expenses, and a list of out-of-stock items.
Information Systems and Identity Management
Summary
The use of Information Technology in healthcare has exposed patients’ information to cyber-attacks. For instance, CHI Health Orthopedics Clinic (Lakeside) reported over 48,000 incidences of health information breaches in a span of 24 months by 30th September 2019. The reported breaches were a result of Hacking and IT incidents. This calls for urgent intervention to ensure that patients’ data is secure, as such incidents have a tremendous impact on the privacy of the affected patients.
Comparing Relational Databases to Spreadsheets
Strengths and Weaknesses of Building a Database Application Using a Relational Database vs. Using a Sprea
DTL Power Cyber Sector Risk Profile
In the risk profile report, the primary targets for cybercriminals are Australia’s DTL power and the United States federal government. DTL specializes in electricity generation and making various industrial dampers whose application in the power generation companies is vast. In contrast, the U.S. federal government is an essential entity that ensures the proper running of socioeconomic and political aspects of the United States. Collapsing DTL Power services has severe implications for businesses and critical systems that rely on electricity to run while targeting the federal government, which risks the release of valuable and highly sensitive information to the US’s enemies or the encryption of important data for ransom. Therefore, cybersecurity personnel must create stringent policies and implement them to protect against illegal access and tampering with user information. Various governments have created such policies globally to prevent specific cyber events such as hacking and fraud, the collapse of business service provision contributing to massive financial losses, and the creation of mitigation policies that aim at business continuity. Cybersecurity policies advocate for the appropriate and professional behavior of information technologists, a critical component of cybersecurity. Assessment of DTL power’s vulnerabilities gives insight into the design of holistic profiles for computing systems and protects them from cyber threats. This report will, in the subsequent sections, detail possible cyber risks and discuss appropriate defense strategies.
dsheet
Comparing Relational Databases to Spreadsheets
Strengths and Weaknesses of Building a Database Application Using a Relational Database vs. Using a Spreadsheet
Comparing Relational Databases to Spreadsheets
Strengths and Weaknesses of Building a Database Application Using a Relational Database vs. Using a Spreadsheet
The selected article applies cloud computing and fog nodes to conduct IoT big data analytics for smart homes (Yassine et al., 2019). Smart homes provide large amounts of data from interconnected devices that can be used to enhance user experience. As a result, innovative IoT is used to capture user data that is later handled by cloud systems and fog nodes to facilitate data-driven services. The developed system further seeks to solve the issues of resource demands for offline and online data processing and storage.
The selected article applies cloud computing and fog nodes to conduct IoT big data analytics for smart homes (Yassine et al., 2019). Smart homes provide large amounts of data from interconnected devices that can be used to enhance user experience. As a result, innovative IoT is used to capture user data that is later handled by cloud systems and fog nodes to facilitate data-driven services. The developed system further seeks to solve the issues of resource demands for offline and online data processing and storage.
You have been hired as an experienced network engineer to design a network that will integrate SNMP, Netflow, and syslog to monitor network health. The wired network consists of five departments in a two-story building using IPv4 currently. Research and create a list of requirements for deploying SNMP, Netflow, and syslog into the network with minimal impact on users and customers. Including all three services in the network may require new IP addresses to be allocated. Make sure new IP addresses are listed in the requirements.
Write a minimum 4-page paper and draw a network diagram that will be inserted into your plan to present to your manager, who has a technical background, that details your plan and your timeline for implementation.
Using the templates and sample documents provided alongside the Project 1 instructions, develop an Enterprise Key Management Policy. The policy governs the processes, procedures, rules of behavior, and training for users and administrators of the enterprise key management system.
Superior Healthcare Enterprise Key Management Policy
Research similar policy documents used by other organizations and adopt an appropriate example to create your policy.
In the previous course, you learned how security professionals employ cryptography, a system of algorithms that hide data. You learned systems can be unlocked with a key provided to those who need to know that data. An important part of cryptography is how to manage these keys to the kingdom. This involves learning and understanding enterprise key management systems and concepts.
Cryptography is the application of algorithms to ensure the confidentiality, integrity, and availability of data, while it is at rest, in motion, or in use. Cryptography systems can include local encryptions at the file or disk level or databases. Cryptography systems can also extend to an enterprise-wide public key infrastructure for whole agencies or corporations.
The following are the deliverables for this project:
Deliverables
- Enterprise Key Management Plan: An eight- to 10-page double-spaced Word document with citations in APA format. The page count does not include figures, diagrams, tables, or citations.
- Enterprise Key Management Policy: A two- to three-page double-spaced Word document.
Project 1: Enterprise Key Management
Step 1: Identify Components of Key Management
Key management will be an important aspect of the new electronic protected health information (e-PHI). Key management is often considered the most difficult part of designing a cryptosystem.
Choose a fictitious or an actual organization. The idea is to provide an overview of the current state of enterprise key management for Superior Health Care.
Review these authentication resources to learn about authentication and the characteristics of key management.
Security Assessment Report
An information system refers to the different systems that are used to collect, analyze, and process information. The information system of an organization consists of the computer system hardware, computer software, databases, the human resources in the organization, and the computer network (“Types of Information Systems”, n.d). One of the components of the computer software component of an information system is the operating system. An operating system is defined as the software that is responsible for the functioning of the different hardware in the system as well as the management of the different application software that can be installed in the system. The operating system is vulnerable to different types of threats
Training Module – Network Configuration
The correct setup of a network should allow for the communication of all network activities within the network for analysis by the network administrator. Setting up Syslog, which is a protocol for the collection and recording of all system actions, is important. This log can be made even more efficient if all the computers on the network have the same exact time allowing logs to carry a timestamp. This can be achieved through setting up a network time protocol (NTP). A network address portal (NAT) is also essential for the communication of computers on the internal network to the Internet using only one address (Angelo, 2019).
From:
Date:
Subject: Customer Relationship Management
Customer relationship management is a model or strategy that deals with customer satisfaction and retention. One of the ways to modify the CRM for the better is to reward loyalty. Rewarding loyalty will increase customer retention as customers will look forward to receiving rewards for their loyalty. For the customer relationship management model to be moved to mobile platforms, the model must be mobile-friendly to increase readability. To increase modularity, the CRM can be divided into different partitions, which can be accessed and edited separately with a table of contents for easy access to all the pages of the CRM. The use of an attractive color scheme and attractive font makes the customer relationship management model more attractive to the eye and increases its readability (Juanamasta et al., 2019)
There are six steps to the project, and the project as a whole should take about two weeks to complete. Begin with the workplace scenario and then continue to Step 1
Step 1: Develop Functional Requirements for Videoconferencing
The first step in your proposal for a secure videoconferencing system is to develop a set of functional requirements for videoconferencing that you believe the media company will need based on its geographic dispersion and business needs.
In developing those requirements, research three videoconferencing solutions such as Skype, GotoMeeting, Polycom, and Cisco Webex and explain their capabilities, advantages, and disadvantages. Identify costs as well as implementation and support requirements.
The functional requirements and the three possible solutions will be a section of your Proposal for Secure Videoconferencing. In the next step, you will review the challenges of implementing those solutions.
Step 2: Discuss Implementation Challenges
In the previous step, you outlined the requirements for secure videoconferencing for the company and outlined three potential solutions. Part of your final proposal should also include the advantages and disadvantages of the implementation options for the three systems you selected. This section of the proposal also must include the changes the media company will need to make to implement the systems.
Additionally, explain how system administration or privileged identity management will operate with these systems. You will also need to examine how data exfiltration will occur with each of the new systems.
The changes to the systems and challenges for the implementation of these potential solutions will be an important section of your Proposal for Secure Videoconferencing. In the next step, you will take a closer look at the track records of each of the potential videoconferencing vendors.
Step 3: Identify Vendor Risks
You’ve finished outlining the pros and cons of three videoconferencing systems. Now, it’s time to take a close look at how they serve their clients. This will take some research. Look at the systems’ known vulnerabilities and exploits. Examine and explain the past history of each vendor with normal notification timelines, release of patches, or work-arounds (solutions within the system without using a patch). Your goal is to know the timeliness of response with each company in helping customers stay secure.
Analysis of Research Methods and Theories
Wearable health technologies, particularly smartwatches, have emerged as transformative tools in the medical field. The integration of these technologies brings forth a paradigm shift, promising enhanced diagnostics, continuous patient monitoring, and improved treatment adherence. However, the adoption of wearable technology is not without challenges. This paper explores the IT business problem associated with the attitudes and behaviors of individuals in regard to wearable technology, focusing on an article by Dastan (2016). Additionally, insights from two additional sources, Jat & Grønli (2023) and Dinh-Le et al. (2019),
The study by Dastan (2016) on the adoption and use of wearable technology is guided by the Technology Acceptance Model (TAM). The framework makes the assumption that two important factors influencing a person’s intention to use technology are perceived utility and ease of use. The researchers employed Technology Acceptance Modelling (TAM) to methodically investigate and assess the attitudes, perceptions, and obstacles associated with the implementation of wearable technologies
Question 
Post a two-paragraph posting in which you do the following:
Read the attached snippets taken from the DIT/DBA Dissertation Chapter Guides. (pdf) Then, do the following.
Describe briefly a topic that you have considered for use as your topic in this program and explain why.

Smart Watch in the Medical Field
Discuss, briefly, one or two articles you found through online research or in the Capella Library that discuss the topics that interest you. Cite those articles using APA style and formatting.
Small Office Home Office (SOHO) networks and other networks contain various network nodes that make them mixed networks. For example, SOHO networks could contain printers, smart TVs, smartphones, tablets, PCs, laptops, routers, VoIP phones, switches, routers, and DHCP servers (Kavalaris & Serrelis, 2015). Larger office networks could contain more devices, including IP cameras, biometric devices, and network storage devices. Though all those network devices are found in a single network, they could be running on different operating systems. For example, tablets could be running on Windows 8, laptops on MAC OS, PCs on Linux, smartphones on iOS, and routers on Linux.
As the Chief Information Security Officer, I suggest the following for a Hospital Business Continuity Plan (BCP).
Executive Overview: Be precise and detailed and provide a thorough understanding of the program.
Document Change Control: The table should be completed.
Introduction: Include the overview, plan scope, and applicability that evaluate the appropriateness of cybersecurity frameworks for developing a cybersecurity program to align with business needs, plan objectives, and plan assumptions. Analyze various cyber threat models used to identify and protect against cybercrime threat vectors, motivations, and ideologies.

Hospital Business Continuity Plan for Systems
Risk Assessment Matrix: Complete a Risk Assessment Matrix. Evaluate system risks, threats, vulnerabilities, practices, and processes to ensure the safety and security of the hospital information systems.
Critical Business Functions Overview: Detail components that are critical to business operations and provide a clear understanding of what the program is designed to address.
Note: A minimum of six scholarly resources are needed.
Electronic Waste Problem
Electronic waste or e-waste are used electronic components that are not of use anymore or have reached their natural expiry. The disposal of such waste is both capital-intensive and time-consuming due to the quantity of electronic devices used globally. It has been recorded that there are more cellular devices than there are people, and the average cell phone has a lifespan of approximately one year
Wireless Networks – Wireless Survey
Wireless networks are a group of interconnected devices that are not physically linked to each other but rather use a wireless link. These devices can then be connected to the internet through a router or modem. Wireless networks are difficult to manage as many items can change the effective range and strength of a wireless network. For instance, the placement of a metal object in front of any wireless transmitter can greatly affect the effectiveness of a wireless network. In order to gain the most out of wireless networks, technicians conduct wireless surveys. Radiofrequency, or wireless survey as it is commonly referred to, is the process of preparing or planning for the placement of wireless equipment in order to make the most of the resources while ensuring all the required locations are covered by the WIFI.
Mobile applications have become commonplace in the modern world due to their ease of use and convenience. Some of the main features of the mobile expense tracker app include security, simplicity, flexibility, user feedback and updates. Security is an important feature since the expense tracker will contain personal information such as banking details, user name and address. It is thus important to keep this information away from malicious users as it can be used to defraud the mobile app user of his or her finances as well as other assets. The flexibility or adaptability of a mobile application refers to the ability of the mobile application to function well under all mobile operating systems, such as Android, IOS, and Windows (Jacob, 2019). Flexibility allows the user to use the application despite the operating system they have on their mobile phone, allowing for a larger number of users. User feedback allows the application developer to understand the user’s point of view as well as the features they would want to be added or removed from the application. User feedback can be given from a textbox which will be accessed by clicking on the feedback link on the mobile application user interface. Updates allow the mobile application to be modified and improved upon after receiving user feedback. Updates allow the mobile application to get better with time instead of maintaining the status quo or becoming outdated. Simplicity as a mobile feature allows the user to perform the required actions with little effort and strain. Simple application design keeps the user from getting frustrated and losing attention before completing the task at hand. Simplicity in the design of the mobile application also makes the development of the application easier (Martinez et al., 2020).
Mobile applications have become commonplace in the modern world due to their ease of use and convenience. Some of the main features of the mobile expense tracker app include security, simplicity, flexibility, user feedback and updates. Security is an important feature since the expense tracker will contain personal information such as banking details, user name and address. It is thus important to keep this information away from malicious users as it can be used to defraud the mobile app user of his or her finances as well as other assets. The flexibility or adaptability of a mobile application refers to the ability of the mobile application to function well under all mobile operating systems, such as Android, IOS, and Windows (Jacob, 2019). Flexibility allows the user to use the application despite the operating system they have on their mobile phone, allowing for a larger number of users. User feedback allows the application developer to understand the user’s point of view as well as the features they would want to be added or removed from the application. User feedback can be given from a textbox which will be accessed by clicking on the feedback link on the mobile application user interface. Updates allow the mobile application to be modified and improved upon after receiving user feedback. Updates allow the mobile application to get better with time instead of maintaining the status quo or becoming outdated. Simplicity as a mobile feature allows the user to perform the required actions with little effort and strain. Simple application design keeps the user from getting frustrated and losing attention before completing the task at hand. Simplicity in the design of the mobile application also makes the development of the application easier (Martinez et al., 2020).
The internet is an interconnection of many small networks. This interconnection forms an extensive interconnection that requires several network devices configured for different purposes (Greenstein, 2020). One of the network devices used in the interconnection is a router. Routers are layer three devices used to forward packets from one network to another (Greenstein, 2020). Therefore, a router would be required for two or more networks to communicate. A router is placed at the gateway of each internal network. For security purposes, routers are configured with access control lists to ensure that only authorized packets can flow in and out of a network (Greenstein, 2020).
The internet is an interconnection of many small networks. This interconnection forms an extensive interconnection that requires several network devices configured for different purposes (Greenstein, 2020). One of the network devices used in the interconnection is a router. Routers are layer three devices used to forward packets from one network to another (Greenstein, 2020). Therefore, a router would be required for two or more networks to communicate. A router is placed at the gateway of each internal network. For security purposes, routers are configured with access control lists to ensure that only authorized packets can flow in and out of a network (Greenstein, 2020).
-
Business Continuity Plan – Needs and Systems for Recovery after a Cyberattack Event
Introduction
Ransomware attacks on the nation’s summit systems lead to a loss of system and data confidentiality, integrity, and availability. The Reveton ransomware denied summit attendees access to conference data, and the computer screens displayed a message indicating a system hack that outputs a message mimicking federal law enforcement authority. Notably, ransomware attacks evolve quickly, and there is no particular framework for combatting new attacks. If a system is hacked, one primarily has two options: pay the ransom or attempt system recovery by rolling back to a previous backup point. Hackers cannot be trusted to release system resources once the ransom is paid. With this in mind, the system’s protection will rely heavily on historical data copies and a wide array of protection mechanisms, as detailed below.
-
Standing Operating Procedures – Trojan Horse
Malware’s Details
- Trojan horse is a deceptive code that misleads users of its actual intent.
- The malicious code typically appears to come from a trusted source.
- Its initial presence as a legitimate software was a strategic way of gaining access to the target system.
- An airplane has one hundred and eighty seats, of which sixty are “non-smokers” and numbered from 1 to 60 and one hundred and twenty seats numbered from 61 to 180 “smoker”. Design a pseudocode that allows the reservation of seats on the plane and stops half an hour before the departu
-
Playbook Threats – Threats Posed by Online Interaction
Phishing
- Clicking unwarranted emails could possibly lead to phishing.
- This is a threat in which untrusted parties masquerade as legitimate people to purposely fetch sensitive information.
- It typically occurs in digital communication and is a major cybersecurity issue.
- It can either be perpetrated through instant messaging or email spoofing.
- Email spoofing occurs when one receives an email with a forged address.
- Once the users click on the email, they might be directed to deceptive websites that seem authentic (Arachchilage, Love & Beznosov, 2016).
- They are then requested to enter personal details and other pertinent information.
- By doing so, they end up exposing the firm’s data contrary to the company’s wish.
- re of the plane, at which time the waiting list will open.
- An airplane has one hundred and eighty seats, of which sixty are “non-smokers” and numbered from 1 to 60 and one hundred and twenty seats numbered from 61 to 180 “smoker”. Design a pseudocode that allows the reservation of seats on the plane and stops half an hour before the departure of the plane, at which time the waiting list will open.
- An airplane has one hundred and eighty seats, of which sixty are “non-smokers” and numbered from 1 to 60 and one hundred and twenty seats numbered from 61 to 180 “smoker”. Design a pseudocode that allows the reservation of seats on the plane and stops half an hour before the departure of the plane, at which time the waiting list will open.
- Each student of a degree in Computer Science has grades corresponding to eight different subjects and may not have a grade in any subject. Each subject corresponds to a certain coefficient. Write a pseudocode to calculate the average of each student.
- Modify the algorithm to obtain the following means:
Write the pseudocode to produce a bill for cell phone charges. Data fields will include date, number called, number of minutes, and cost (rate × minutes). Data should be loaded into an array. Include totals for the number of minutes and cost.
A weather station provides a couple of daily temperatures (maximum, minimum) (it is not possible for either or both temperatures to be 9 degrees). The end temperature pair is 0, 0. Create a program that determines the number of days, whose temperatures have been provided, the maximum and minimum averages, the number of errors – temperatures of 9 ° – and the percentage they represented.
It is intended to read all the employees of a company – located in a COMPANY file – and at the end of reading the file, shows the following message: “There are ## workers over 65 years of age ” (## is the number of workers that are over 65 years old).
In a company work n employee whose salaries range between $ 100 and $ 500, create a program that reads the salaries that each employee receives and report how many employees receive between $ 100 and $ 300 and how many receive more than $ 300. In addition, the program must report the amount the company spends in salaries to staff.
Discussion – Loops and Arrays
Write pseudocode for a program that will record weather-related data for any month or months.
- Input could be month name(s)
- for loop inputs could be:
- High and low temperatures
- Precipitation
iii. Humidity.
This paper is to familiarize you with the Linux operating system. Some have heard of Linux before; however, they have never had the opportunity to utilize the operating system. This assignment is made to help you understand the similarities and differences between Linux, Windows, and Mac.
Assignment Instructions
Linux has a very unusual background and origin. The founder is very unique as well. This uniqueness has also led to the massive explosion of distributions of Linux. Unlike Windows®, where there are seven or eight different versions, there are thousands of distributions out there.

The Linux Operating System- Linux Beginnings
The upper management of your company, Simply Something, has heard about Linux and is wondering why the company has not adopted it. The only thing they know is that it is free and can save the company large sums of money in licensing fees. The CIO needs you to create a briefing to present to management on Linux. Remember, when you are preparing this document, that the company currently uses Windows® and Macs®, uses Microsoft® Office® for documents, has remote users (laptops), and uses Adobe® Photoshop® for editing pictures for the Web.
Standing Operating Procedures – Trojan Horse
Malware’s Details
- Trojan horse is a deceptive code that misleads users of its actual intent.
- The malicious code typically appears to come from a trusted source.
- Its initial presence as a legitimate software was a strategic way of gaining access to the target system.
- The software ultimately seeks to take control of the computer, and the first version of its kind was established in 1975.
- It is usually designed to steal, disrupt, damage, or initiate other harmful actions on the network, system, or data (Easttom, 2019). Our assignment writing help is at affordable prices to students of all academic levels and disciplines.
Write a 2- to 3-page report using Microsoft® Word to your management as a software engineer. Detail the following:
Describe how you will utilize the Lincoln index to rectify the test results given by the testers and deliver a bug-free website to your client.
Describe the 3 types of tests your team plans to run on the e-commerce website. How will these tests help to reduce the bugs identified by the testers?
Provide a brief description of 2 research tools, each of which you would recommend for test automation tools, version control, and continuous integration and delivery, and explain how they will help improve the maintainability of your application.
Imagine that you are hired to create a basic database and a basic report for a school. In the SQL comments at the top of the script, write a short description of the school and how the database is used by the school personnel. (some examples: “This database is used to register new students at Dog Obedience School”, “The Beauty Academy database determines how much revenue each class generates”, “Lucky Brake Driving School Database tracks accident rates across classes”, “CUNY SPS BSIS program could track pe
Question 
Your company received a request from one of its clients to design a website. You started with the process of designing a typical e-commerce website with a user log in, a payment portal, and a product display section.

Using The Lincoln Index for Software Testing
Your e-commerce website involves online payments. Testing is an important component for websites that involve payments. You assigned two testers to test the website. The testers tested the site and found 7 and 5 bugs, respectively, but nothing in common.
r cent of students working in the field that have taken this course”, etc.
You should create and populate tables – using SQL exclusively – for Courses and Students. Each table should contain at least four or five rows.
You are encouraged to add one or more new columns that would be of interest to the people who use the information in your database, as you have described in number one above.
Write a SQL Query that shows which students are taking which courses.
You need to create an additional table to fulfil the additional requirements liste
Imagine that you are hired to create a basic database and a basic report for a school. In the SQL comments at the top of the script, write a short description of the school and how the database is used by the school personnel. (some examples: “This database is used to register new students at Dog Obedience School”, “The Beauty Academy database determines how much revenue each class generates”, “Lucky Brake Driving School Database tracks accident rates across classes”, “CUNY SPS BSIS program could track per cent of students working in the field that have taken this course”, etc.
You should create and populate tables – using SQL exclusively – for Courses and Students. Each table should contain at least four or five rows.
You are encouraged to add one or more new columns that would be of interest to the people who use the information in your database, as you have described in number one above.
Write a SQL Query that shows which students are taking which courses.
You need to create an additional table to fulfil the additional requirements liste
Python programming is recommended for cybersecurity (Wang et al., 2020). It offers web security for web browsers. Because of its highly effective data security features, Python is used in computer vision, big data, robotics, automation testing, and machine learning (Wang et al., 2020). Python also offers high memory safety. This is implemented through MesaPy. The Python programming language also has a simple syntax that makes
Demonstrate an understanding of basic C++ programming concepts by completing the following:
• Program: Create a simple C++ console application that will write a program that will take string input from a user. Your program should reverse the string and then print the output to the screen. Take input from the user 3 times for varying string lengths.
String Input Console Application and Program Analysis- Program Analysis
• Program Analysis: Given your program implementation, discuss and identify the possible vulnerabilities that may exist. If present, discuss solutions to minimize the vulnerabilities. Then, discuss and identify possible problems that can result in errors for string manipulation of data.
This course started my doctoral journey, a pursuit characterized by difficult academic challenges and growth opportunities. This reflective essay aims to illustrate how my interactions with classmates in the residency course have helped me understand the struggles of doctoral students from the beginning of this term to the end.
The Internet is a dangerous place as it has turned into a battlefield where companies have to fight to protect their data from attackers. When it was first created, the Internet was meant to be a way for people to share information and communicate with each other. In recent times, it has become an incredibly complex digital landscape used by nation-states, criminal organizations, and hacktivists to engage in cyber espionage and warfare (Freet & Agrawal, 2017). Unfortunately, every company holds valuable assets and customer data, which makes them a valuable target for these hackers. One of the most common tactics attackers use is Advanced Persistent Threats (APTs). These threats can last weeks or even months without detection.
Report Analysis-Analysis of Market Trends in the Automotive Industry
Target Audience of the Report
The selected report focuses on software engineering methodologies to discern their relevance in life. The author focuses on Open Source Software (OSS) and Closed Source Software (CSS), with Linus and Agile models being the demonstration paradigms. The report is primarily tailored for people with a vested interest in discovering and comprehending the concepts of engineering methodologies. This population is composed of computer scientists, software engineers, IT technicians, and students. It is further simplified to suit people with a less technological background but who have vested interests in software programming. Nevertheless, the derived concepts suit the general society, including mothers, fathers, soccer players, and managers. Lennon (2016) strives to conceptualize the ideas of software engineering beyond their complicated regular use. For this reason, the target audience is autonomously a broad population.
Discussion – Computer Networking
The different forms of government play different roles in combating terrorism. The federal government is tasked with sharing information with other international agencies against terrorism. It is also the federal government’s role to protect border points from infiltration by terrorist organizations; this role is played in conjunction with border state governments. On the other hand, the State and local governments act as the first response against any acts of terrorism. These governments are also able to collect more detailed information on the local community against any terrorist organization within the community.
2.4 Related Works
In 2019, the Roll-on/roll-off (RoRo) company was advised to implement a real-time tracking system (M’handa et al., 2019). This would replace its periodically updated tracking system. RoRo was experiencing problems similar to those that are currently being experienced by Swift Services Company. The two companies used staff to manually update the tracking system. However, RoRo transports cargo on the sea while Swift Services does not (M’handa et al., 2019). Real-time tracking would improve efficiency at RoRo because, previously, cargo details would only be updated at the port. This made it difficult to estimate cargo traffic and offloading, especially when ships arrived simultaneously. But with real-time tracking, the staff at the port would identify in advance the ship that would arrive first and its contents (M’handa et al., 2019). Making the process of offloading efficient.
Discussion – Computer Networking
The different forms of government play different roles in combating terrorism. The federal government is tasked with sharing information with other international agencies against terrorism. It is also the federal government’s role to protect border points from infiltration by terrorist organizations; this role is played in conjunction with border state governments. On the other hand, the State and local governments act as the first response against any acts of terrorism. These governments are also able to collect more detailed information on the local community against any terrorist organization within the community.
Cybersecurity focuses on protecting internetworked systems from exploitation by malicious persons (Seemma, Nandhini & Sowmiya, 2018). These systems include data, hardware, and software. There are several ways in which internetworked systems could be exploited, and one of them is through user activities.
Essential Metrics for Data-Driven Decision Making- Building Skills in Data Acquisition and Reporting
Metrics in an organization are used to ensure that the organization performs optimally. Such metrics constantly measure an organization’s performance to facilitate improving performance. There are some common organization metrics used throughout the world. For example, in Ireland, market share, return on investment, customer satisfaction, and profitability are used by a majority of the organizations (Liang, Gao & Ding, 2018).
Incorporate the following into your responses in the template:
Subjective: What details did the patient provide regarding their chief complaint and symptomology to derive your differential diagnosis? What is the duration and severity of their symptoms? How are their symptoms impacting their functioning in life?
Objective: What observations did you make during the psychiatric assessment?
Assessment: Discuss the patient’s mental status examination results. What were your differential diagnoses? Provide a minimum of three possible diagnoses with supporting evidence, listed in order from highest priority to lowest priority. Compare the DSM-5 diagnostic criteria for each differential diagnosis and explain what DSM-5 criteria rule out the differential diagnosis to find an accurate diagnosis. Explain the critical-thinking process that led you to the primary diagnosis you selected. Include pertinent positives and pertinent negatives for the specific patient case.
NR NR224 Final Exam Concept Blueprint
NR 224: Final Exam Concept Blueprint
A. Medication Administration Chapter 31
1.) 7 rights of medication administration
A Modernized Marketing Information System: Streamlining Operations and Enhancing Efficiency
This essay outlines the design and benefits of a modernized marketing information system (MIS) for a hypothetical organization. The proposed system aims to address the limitations of the current system, streamline marketing operations, and enhance data-driven decision-making.
When developing a software tool for a small group of users within the marketing department, the Agile software development methodology emerges as the optimal choice. This approach offers several key advantages that align perfectly with the specific requirements of this scenario.
Firstly, Agile's iterative and incremental nature allows for rapid development cycles and continuous feedback loops. The team can build and release small, functional parts of the software quickly, receiving valuable input from the marketing team at each stage. This ensures that the software is built to meet their specific needs and avoids wasting time on features that aren't valuable.
Secondly, Agile's inherent flexibility is crucial for adapting to the dynamic nature of marketing needs. Marketing strategies and requirements can shift quickly, and Agile allows the development team to adjust the plan accordingly, ensuring the software remains relevant and effective.
Thirdly, Agile emphasizes collaboration between developers and users. This ensures the marketing team is actively involved in the development process, providing valuable input and ensuring the software meets their expectations. This collaborative approach fosters a sense of ownership and ensures the final product aligns perfectly with the marketing team's vision.
Within the Agile framework, the Scrum implementation methodology provides a structured and efficient approach. Scrum utilizes short development cycles called sprints, daily stand-up meetings, and regular reviews, keeping the project on track and allowing for continuous improvement. This structured approach ensures that progress is made consistently, and any potential roadblocks are identified and addressed promptly.
A prime example of a company that utilizes its own software for marketing is HubSpot. HubSpot offers a comprehensive suite of tools for marketing automation, email marketing, CRM, and more. They likely employ an Agile methodology to develop and improve their software, allowing them to quickly adapt to the evolving needs of their users. This agile approach enables HubSpot to stay ahead of the curve in a rapidly changing marketing landscape.
In conclusion, for a small group of users in the marketing department, the Agile methodology, with Scrum implementation, is the ideal approach for software development. This combination fosters collaboration, flexibility, and continuous improvement, ensuring the software is tailored to the specific needs of the marketing team and delivered efficiently. By embracing Agile principles, organizations can empower their marketing teams with innovative software tools that drive success
The main difference between the two databases is their size and approach. While a data warehouse serves as the global database of a business and stores data about any aspect of the company, a data mart stores a small amount of data related to a specific business department or project. Similarly, a data warehouse collects data from a wide variety of sources, whereas a data mart typically collects data from the central database, the data warehouse. This, in turn, means that a data warehouse has a much larger storage capacity than a data mart and a much more complex and difficult to design architecture. In addition, the implementation process of a data warehouse is more complex and time-consuming —it usually takes several months or even years— while that of a data mart can be solved in a few months since it gathers a much smaller amount of data and it has a simpler structure.
Carrying on with the example of the educational system, we could say that a data warehouse is the place where all the documents of an educational center are stored, while a data mart would be the place where each teacher or group of teachers keep the documentation relevant to their subject.
Below, we explore in more detail the main distinctions between a data warehouse and a data mart:
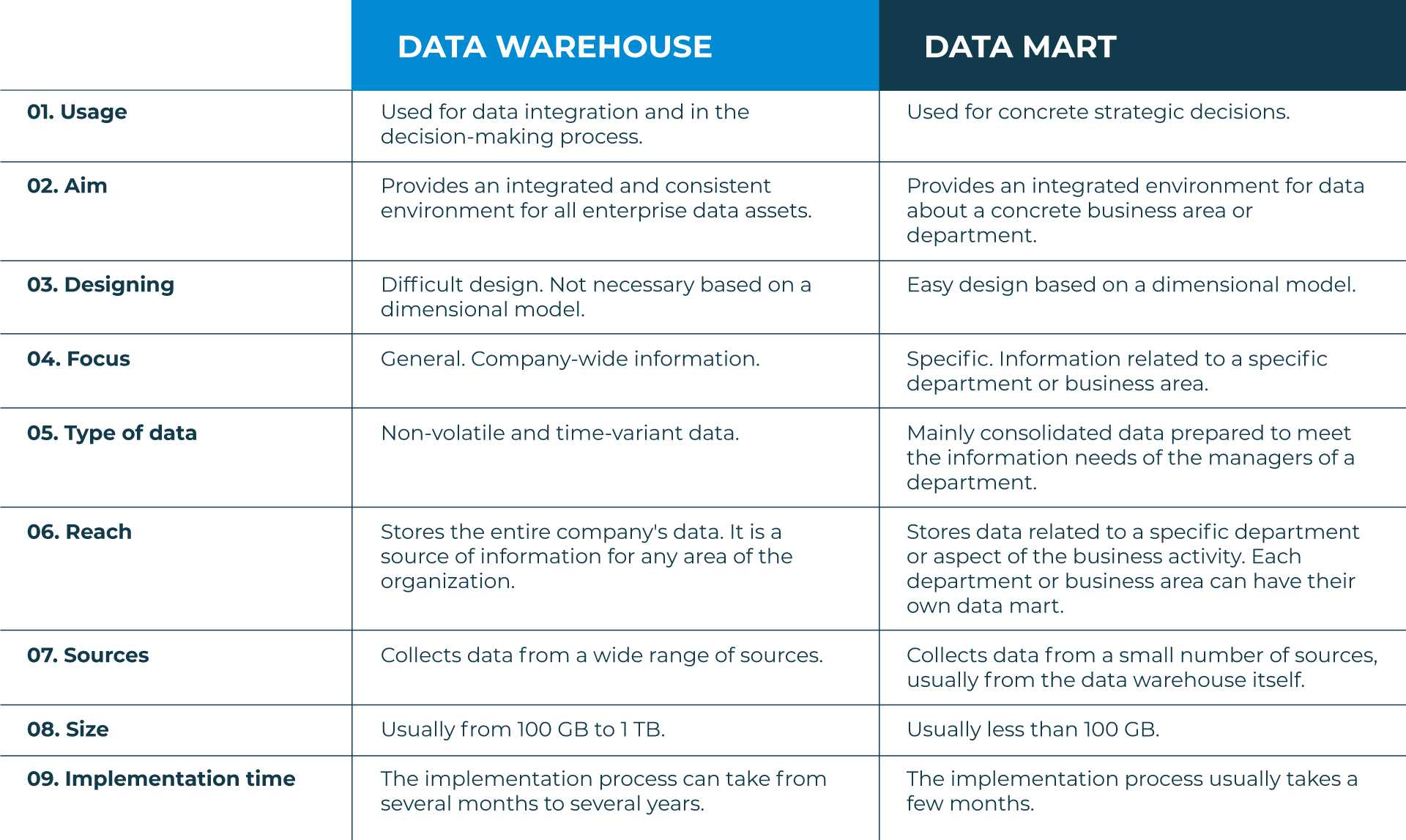
Referring to the main differences between a data warehouse and a data mart, while a data warehouse is used as an organisation's central data repository, a data mart is a more specific data warehouse.
-
A data warehouse facilitates the data integration and general business decision making process of the company, while a data mart assists in more specific strategic decision making.
-
The goal of a data warehouse is to provide an integrated and consistent environment for all of the company's data assets. In contrast, a data mart is an integrated environment for data pertaining to a specific business department.
-
In other words, a data warehouse has a general approach and stores information and data relating to the entire company. In contrast, a data mart has a specific focus and integrates information from a specific business area or department.
-
The design process of a data warehouse is complex and does not have to be based on a dimensional model. On the other hand, the design process of a data mart is easier and is always based on a dimensional model.
-
In terms of data types, a data warehouse contains detailed data that is non-volatile in structure and can vary over time. A data mart, on the other hand, mainly contains consolidated and ready-made data to meet the information needs of department or business area managers.
-
A data warehouse and a data mart are quite different in scope. A data mart is a narrow database, in the sense that it stores data relating to a particular department or aspect of the business. Each department or business area can have its own data mart. A data warehouse, on the other hand, stores data linked to the entire company and to any aspect of the business activity. It acts as a source of information for any area of the organisation.
-
In this sense, a data warehouse collects data from a large number of sources. Typically, a data mart stores data from a small number of sources and, in fact, the main source of origin of a data mart is usually the central data warehouse.
-
data warehouse typically has a size or capacity ranging from 100 GB to 1TB. In contrast, a data mart typically has a capacity of less than 100 GB.
-
Finally, a data warehouse requires an implementation period of several months to several years. In contrast, a data mart can be implemented in a few months.
Key differences: data warehouses vs. data lakes
A data warehouse and a data lake are two related but fundamentally different technologies. While data warehouses store structured data, a lake is a centralized repository that allows you to store any data at any scale. A data lake offers more storage options, has more complexity, and has different use cases compared to a data warehouse. Key points of difference are given below.
Data sources
Both data lakes and warehouses can have unlimited data sources. However, data warehousing requires you to design your schema before you can save the data. You can only load structured data into the system. Conversely, data lakes have no such requirements. They can store unstructured and semi-structured data, such as web server logs, clickstreams, social media, and sensor data.
Preprocessing
A data warehouse typically requires preprocessing before storage. Extract, Transform, Load (ETL) tools are used to clean, filter, and structure data sets beforehand. In contrast, data lakes hold any data. You have the flexibility to choose if you want to perform preprocessing or not. Organizations typically use Extract, Load, Transform (ELT) tools. They load the data in the lake first and transform it only when required.
Data quality
A data warehouse tends to be more reliable as you can perform processing beforehand. Several functions like de-duplication, sorting, summarizing, and verification can be done in advance to assure data accuracy. Duplicates or erroneous and unverified data may end up in a data lake if no checks are being done ahead of time.
Performance
A data warehouse is designed for the fastest query performance. Business users prefer data warehouses so they can generate reports more efficiently. In contrast, data lake architecture prioritizes storage volume and cost over performance. You get a much higher storage volume at a lower cost, and you can still access data at reasonable speeds.
.b92355dc1f5dead04c2d3778ede8deb44ac84df9.png)
.4a794ed179f7108666c5f41eb937acee11374b44.png)
| Characteristics | Data Warehouse | Data Lake |
|---|---|---|
| Data |
Relational data from transactional systems, operational databases, and line of business applications |
All data, including structured, semi-structured, and unstructured |
| Schema |
Often designed prior to the data warehouse implementation but also can be written at the time of analysis (schema-on-write or schema-on-read) |
Written at the time of analysis (schema-on-read) |
|
Price/Performance |
Fastest query results using local storage |
Query results getting faster using low-cost storage and decoupling of compute and storage |
|
Data quality |
Highly curated data that serves as the central version of the truth |
Any data that may or may not be curated (i.e. raw data) |
| Users |
Business analysts, data scientists, and data developers |
Business analysts (using curated data), data scientists, data developers, data engineers, and data architects |
| Analytics |
Batch reporting, BI, and visualizations |
Machine learning, exploratory analytics, data discovery, streaming, operational analytics, big data, and profiling |
| Learn more about Data Warehouses | Learn more about Data Lakes |
The original data warehouse structured and designed for Indiana University Health is traditional enterprise data warehouse. They …show more content…
Data warehouse has different concepts of data. Each concept is divided into a specific data mart. Data mart deals with specific concept of data, data mart is considered as a subset of data warehouse. In Indiana University traditional data warehouse is unable to create large data storage. Further it shows any errors and imposed rules on data. The early binding method is disadvantage. It process longer time to get enterprise data warehouse (EDW) to initiate and running. We need to design our total EDW, from every business rule through outset. The late binding architecture is most flexible to bind data to business rules in data modeling through processing. Health catalyst late binding is flexible and raw data is available in data warehouse. It process result by 90 days and stores IU data without any errors.
The Evolution of Cybercrime: Impacts, Responses, and Future Challenges
The use of data has become a critical aspect of success in current technology and business environments. According to William and Wijaya (2017), by combining several APIs (Application Programming Interfaces), businesses have been provided with opportunities to access and use huge volumes of information in a bid to improve operations and make better decisions
-
Ransomware is malware designed by recent programmers with malicious intentions where the malware is designed to encrypt important details from the target computer and demand ransom for decryption. The model is designed to enhance the tactical attacks performed by the previous bank Trojans. As a result, it combines various detailed techniques that converge towards victimizing targets by demanding ransoms after interfering with the access of important documents in the victim’s computer. Although malware has existed as a known cyber-attack, its prevalence has occurred in the past two years when large organizations have reported such cases.
-
Introduction
The 21st Century is marked by an unprecedented surge in technological innovation, with robots and machines at the forefront of this transformative wave (Kolade & Owoseni, 2022; Nabila et al., 2021). While these advancements hold the promise of revolutionizing industries, they also cast a shadow of uncertainty over the future of employment. Further, this revolution necessitates educating more people on current technologies to increase productivity in various industries like the textile industry.
-
In the fast-paced realm of Cyber-Psychology, emotional and cultural intelligence are essential factors that shape the success of our organization. As a security practitioner immersed in this dynamic field, I have gained an appreciation for the immense value of emotional and cultural intelligence. This paper aims to explore the significance these intelligences hold within our work organization and address common technical and administrative hurdles faced in day-to-day practice
-
Introduction
In the vast domain of cybersecurity, Access Control stands out as a pivotal component that delineates who can or cannot access resources in a network. Essentially, it is a process that helps safeguard against unauthorized intrusions, ensuring that only those who should have access can obtain it. Like a meticulous guard checking credentials at the door, effective access control systems are integral in the digital world to ward off cyber threats. However, as with all things, no system is infallible